The strategy developed by the U.S. DoD Joint Improvised Explosive Device Defeat Organization (JIEDDO) focuses counter IED efforts using three lines of operation: Attack the Network, Defeat the Device and Train the Force.
’Attack the Network’ is one of the biggest areas where progress has been made. JIEDDO supports units conducting offensive operations through improvements to intelligence collection, information operations, forensic exploitation and surveillance. These initiatives become long-term service programs of record that provide an enduring C-IED capability to the warfighter.
In August 2006 JIEDDO established the Counter-IED Operations Integration Center (COIC) to focus on attacking enemy networks employing and assisting IED supporters, producers, trainers and operators. COIC also provides an avenue for strategic reachback to collaborative, fused, multi-source information and knowledge resources across critical DoD, government, industry, academic organizations and agencies. Through COIC’s fused intelligence products, formerly highly classified intelligence is now available at the secret level, making it accessible to warfighters at the tactical level.
One highly successful program targeting IED networks is the Law Enforcement Professional program. After noting similarities between organized crime and IED networks, JIEDDO funded the LEP program to leverage the knowledge and skill of former law enforcement experts to attack the IED network activities. It has enabled the services to disrupt the vast network by expanding operations beyond emplacers and target the finances, explosives, supply line of parts and the brains that build IEDs.
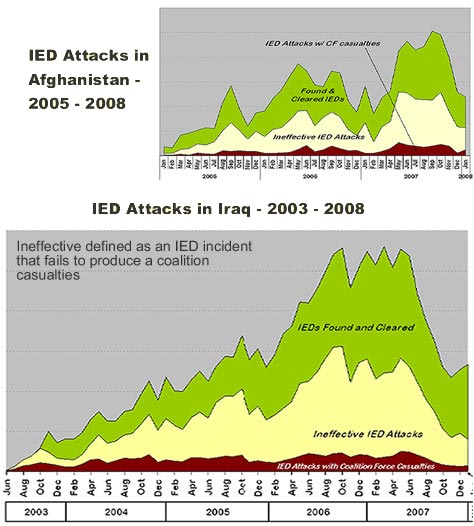
The insurgents who place IEDs in Iraq and Afghanistan are often supported by organized networks that finance their operations, supply critical elements for the production of IEDs, create the devices and plan and execute attacks. The new system implements powerful analytics to gain critical, data driven insight into the structure, character, interactions and methods associated with those networks. By analyzing data from myriad sources the new system can identify and analyze the linkages between individuals and groups that may indicate a support network.
 Text based information resources such as email and articles can be used with text processing applications such as SAS Text Miner (picture here), to uncover information hidden in document collections, by analysing a elements with common intelligence values and predictive models.
Text based information resources such as email and articles can be used with text processing applications such as SAS Text Miner (picture here), to uncover information hidden in document collections, by analysing a elements with common intelligence values and predictive models.
Terrorists Tracks Uncovered by Information Data-Mining
Along its effort to combat the networks supporting the IEDs and their producers and operators, JIEDDO has recently launched a new intelligence collection and analysis system aiming to uncover and target the operational, financial and social networks involved in IED deployment. The system was implemented by system integration specialist SAS and Detica, a developer of data analysis tools.
Detica and SAS combined to provide an analytical solution that addresses the challenges of data access, integration, quality and management. Following this ground work, JIEDDO can now integrate existing data from all relevant sources, and with advanced analytics and reporting capabilities, provide exploitable information to field commanders in theater.
The JIEDDO solution uses several tools, including data and text analysis, predictive modeling and optimization. Analysts and other end users receive detailed intelligence developed using data driven investigative techniques and link analysis based on social network theory. While the concepts are leading edge, it is a proven technical solution currently running in both government agencies and commercial businesses in the UK and the US. Analysts are provided with client tools and customizable report creation and delivery capabilities that provide intelligence in the most appropriate format for decision makers and other end users. The solution is also customizable to be implemented at all levels of security classification.
In the modern and developed world, where most of those support networks operate, government agencies and the business sector generate unprecedented volumes of data. Customer profiles, organizational operational performance, and personal behaviour of individuals are monitored by multiple sevice providers.
Some data resides in structured form in databases or exists as real-time streams. Some exists in unstructured form, for example as e-mails, electronic documents or media files. Whatever the form, there exists huge potential to transform these data into relevant intelligence to improve business decision-making.
Before the solution could be deployed, JIEDDO had to address various data challenges. Until recently, much of the data received from multiple sources in theater, from DOD and other US government agencies, was not integrated or coordinated with data developed by other units or agencies, it usually remained unstructured or lacked a common format or vocabulary. Also, data quality was problematic because of the amount that was manually keyed or handwritten, the lack of standard format and templates, and the variety of sources.
SAS is the leading business intelligence and analytical software specialist, providing services to the business and government customers. Specializing in information-intensive areas of security, fraud containment, risk management, regulatory compliance and customer management Detica is also a supplier of information processing systems to the national security market. The companies developed effective tools to handle huge and complex data sources, building systems that aggregate and analyse data to generate useful and relevant intelligence. “SAS and Detica have worked closely with JIEDDO to create a solution that will work toward helping our armed forces fight back against the most effective weapon in the insurgent arsenal,” concluded Tom Mazich, SAS Vice President of Government Operations.