Since 2001 the CIA has gained political and budgetary preeminence over the U.S. National Security Agency (NSA). The CIA found itself building not just its now infamous drone fleet, but a very different type of covert, globe-spanning force — its strong fleet of hackers. The agency’s hacking division freed it from having to disclose its often controversial operations to the NSA (its primary bureaucratic rival) to draw on the NSA’s hacking capacities.
the CIA has secretly made most of its cyber spying war code unclassified
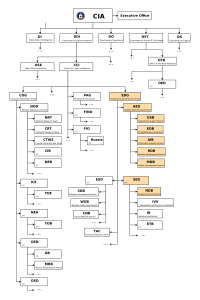
According to the documents released today by Wikileaks, by the end of 2016, the CIA’s hacking division, which formally falls under the agency’s Center for Cyber Intelligence (CCI), had over 5,000 registered users. They had produced more than a thousand hacking systems, trojans, viruses, and other “weaponized” malware, collectively known as “Vault 7”.
Based on the documents released by Wikileaks the organization assesses the scale of the CIA’s hackers activities in 2016 utilized more code than that used to run Facebook. The CIA had created, in effect, its “own NSA” with even less accountability and without publicly answering the question as to whether such a massive budgetary spend on duplicating the capacities of a rival agency could be justified.
But the clandestine cyber operation has even more dangerous side effects – recently, the CIA lost control of the majority of its hacking arsenal, including malware, viruses, trojans, weaponized “zero-day” exploits, malware remote control systems and associated documentation. Once a single cyber ‘weapon’ is ‘loose’, it can spread around the world in seconds, to be used by rival states, cyber mafia and teenage hackers alike. This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA. The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.
Big Brother Is In Your TV and Your Car
The CIA Engineering Development Group (EDG) is responsible for the development, testing and operational support of all backdoors, exploits, malicious payloads, trojans, viruses and any other kind of malware used by the CIA in its covert operations worldwide.
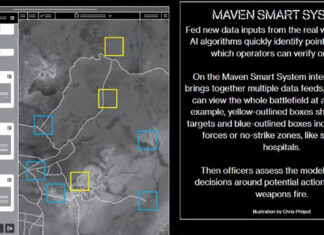
Among the activities described in the recently published documents is a malware which infects smart TVs, transforming them into covert microphones. For example, the “Weeping Angel” developed under a joint US-UK partnership was designed to attack Smart TVs made by Samsung. After infestation, Weeping Angel places the target TV in a ‘Fake-Off’ mode, that bypass the shutdown of the device. While the users think their TV is off, the device is remotely controlled, can record conversations in the room and send them over the Internet to a covert CIA server.
Other attacks were designed to infect control systems used in modern cars and trucks. The purpose of such control is not specified, but it would permit the CIA to engage in nearly undetectable assassinations.
Exploiting Mobile Phones
Mobile Devices are also very vulnerable to attacks developed by the CIA’s Mobile Development Branch (MDB), as they are targeted by many criminal and intelligence agencies worldwide. These devices can easily be turned into tracking and spying devices as well as covertly activating the phone’s camera and microphone.
The CIA invested considerable effort hacking into iPhones, considered more difficult to attack. In 2016 the CIA established a specialized unit to produces malware to infest, control and exfiltrate data from iPhones and other Apple products running iOS, such as iPads. The disproportionate focus on iOS may be explained by the popularity of the iPhone among social, political, diplomatic and business elites. The CIA’s iPhone hacks arsenal includes numerous local and remote “zero days” developed by CIA or obtained from GCHQ, NSA, FBI or purchased from cyber arms contractors such as Baitshop.
A similar unit targets Google’s Android which is used to run the majority of the world’s smartphones, including Samsung, HTC, and Sony. As of 2016, the CIA had 24 “weaponized” Android “zero days” which it has developed itself and obtained from GCHQ, NSA, and cyber arms contractors. These techniques permit the CIA to bypass the encryption of WhatsApp, Signal, Telegram, Weibo, Confide and Cloackman by hacking the “smart” phones that they run on and collecting audio and message traffic before encryption is applied.
Other departments run a very substantial effort to infect and control popular operating systems including Microsoft Windows, Apple OSX and Linux.
As expected, Microsoft Windows users are exposed to multiple local and remote weaponized “zero days,” and air gap jumping viruses such as “Hammer Drill” which infects software distributed on CD/DVDs. Other risks cooked by the CIA include infectors for removable media such as USBs, systems to hide data in images or covert disk areas (“Brutal Kangaroo”) and to keep its malware infestations going. Many of these infection efforts are pulled together by the CIA’s Automated Implant Branch (AIB), which has developed several attack systems for automated infestation and control of CIA malware, such as “Assassin” and “Medusa.”
The CIA also targets the Internet infrastructure and web servers through their Network Devices Branch (NDB). This branch uses automated multi-platform attack tools and malware control systems known as the “HIVE” and “Cutthroat” or “Swindle” – tools covering all common operating systems – Windows, Mac OS X, Solaris, and Linux.
‘Zero-Day’ Tsunami
In the wake of Edward Snowden’s leaks about the NSA, the U.S. technology industry secured a commitment from the Obama administration that the government would disclose to industry serious vulnerabilities, exploits, bugs and ‘zero days’ discovered in information systems and technologies developed by Microsoft, Apple, Google and other US manufacturers. The new documents show that the CIA breached these commitments. Many of the vulnerabilities used in the CIA’s cyber arsenal are pervasive, and some may already have been found by rival intelligence agencies or cyber criminals.
Unlike weapons of mass destruction or major defense systems, cyber ‘weapons’ are, in fact, just computer programs which can be pirated like any other. Since they are entirely comprised of information, they can be copied quickly with no marginal cost. Therefore, securing such ‘weapons’ is particularly challenging since the same people who develop and use them have the skills to exfiltrate copies without leaving traces — sometimes by using the very same ‘weapons’ against the organizations that contain them.
There are substantial price incentives for government hackers and consultants to obtain copies since there is a global “vulnerability market” that will pay hundreds of thousands to millions of dollars for copies of such ‘weapons.’ Similarly, contractors and companies who obtain such ‘weapons’ sometimes use them for their purposes, getting an advantage over their competitors in selling ‘hacking’ services.
Over the last three years the United States intelligence sector, which consists of government agencies such as the CIA and NSA and their contractors, such as Booze Allan Hamilton, has been subject to unprecedented series of data exfiltrations by its workers.
A number of intelligence community members not yet publicly named have been arrested or subject to federal criminal investigations in separate incidents.
Most visibly, on February 8, 2017, a U.S. federal grand jury indicted Harold T. Martin III with 20 counts of mishandling classified information. The Department of Justice alleged that it seized some 50,000 gigabytes of information from Harold T. Martin III that he had obtained from classified programs at NSA and CIA, including the source code for numerous hacking tools.
Once a single cyber ‘weapon’ is ‘loose’ as a massive tsunami, spreading around the world in seconds, and immediately be exploited by peer states, cyber mafia and teenage hackers alike.
One can assume that when developing such powerful cyber weapon, the CIA would keep them highly classified and limit the access to such capabilities on a need to know basis. However, to enable as wide distribution of such malware and exploits as possible, the CIA declassified these tools. The CIA structured its classification regime such that the most valuable part of “Vault 7” was… unclassified! Yes, the CIA’s weaponized malware (implants + zero days), Listening Posts (LP), and Command and Control (C2) systems were all unclassified. Having these weapons unclassified enabled these implants to communicate with their control programs over the internet. (If CIA implants, Command & Control and Listening Post software were classified, then CIA officers could be prosecuted or dismissed for violating rules that prohibit placing classified information onto the Internet.)
Moreover, the vast investment in hacking tools and exploits was contributed freely to the criminal community and foreign cyber agencies, since the U.S. government is not able to assert copyright either, due to restrictions in the U.S. Constitution. This means that cyber ‘arms’ manufacturers and computer hackers can freely “pirate” these ‘weapons’ if they are obtained. The CIA has primarily had to rely on obfuscation to protect its malware secrets.
Developers were instructed to write code that infiltrates target systems, encrypt and exfiltrate data to command and control servers, eliminate any forensic evidence of its activity, evade most well-known anti-virus programs and persist for extended periods in the target machines.