In yet another startling revelation surrounding the continuing saga vilifying the Chinese for involvement in selling counterfeit electronics, research scientists with Cambridge University have released a report claiming they have discovered that a Chinese-built microprocessor in widespread use by the US armed forces comes complete with a built-in “backdoor” that can be reprogrammed.
The microchip in question has been employed in many applications including military weapons, nuclear power facilities, and public transportation systems. The built-in backdoor, according to the Cambridge scientists, cannot be “fixed” and the only remedy is to replace the chip itself.
Chinese companies have long been suspected of producing counterfeit electronic components that have eventually been incorporated into vital US military weapon’s systems placing US national security at risk and endangering the lives of American servicemembers. A US Senate Armed Forces Committee (SASC) report released in May and a General Accountability Office (GAO) report released in March appear to provide irrefutable evidence to support these suspicions.
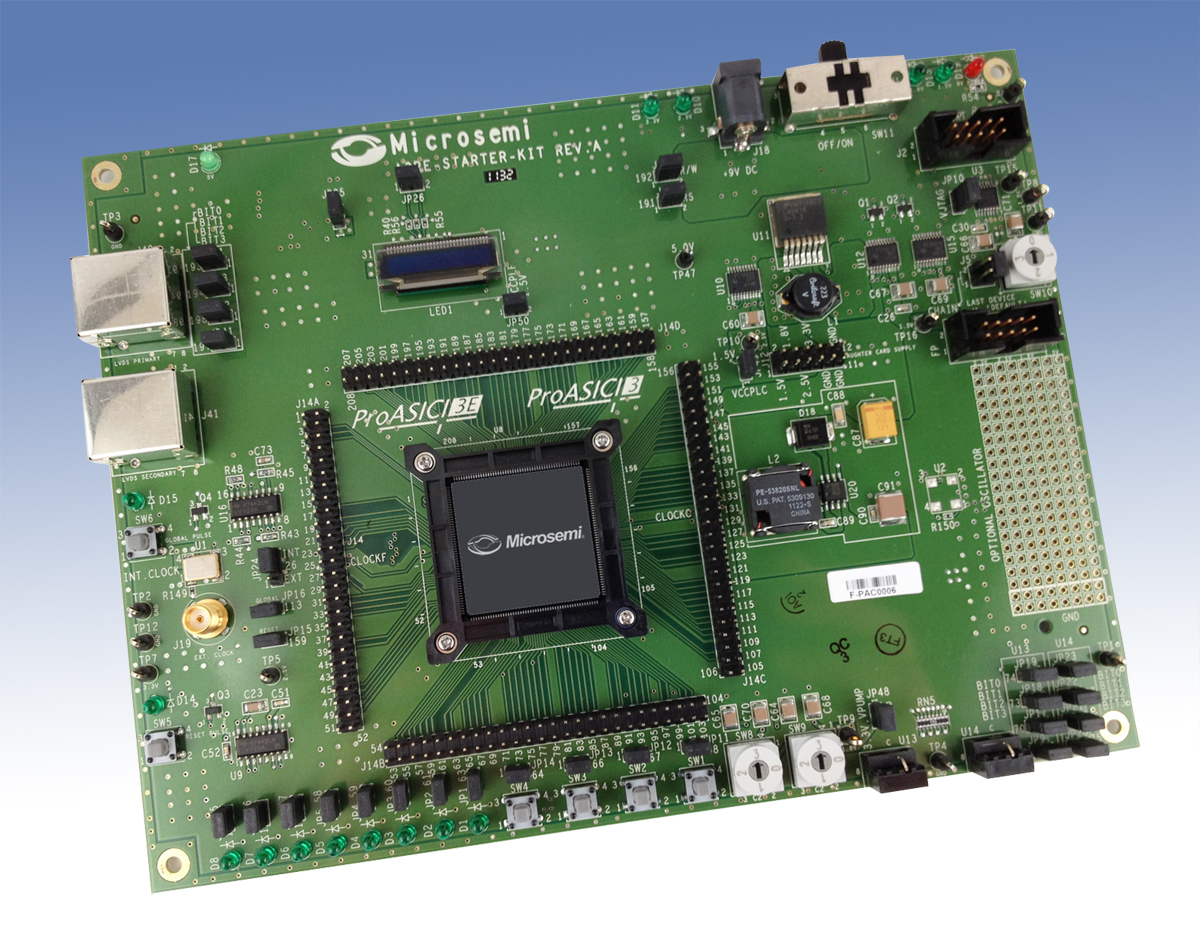
Cambridge scientists focused their efforts on examining the American-designed, Chinese-manufactured ProASIC3 A3P250 microprocessor, a component more commonly known as the PA3 distributed by the Microsemi Corporation of San Jose, California. The PA3 is a Field Programmable Gate Array (FPGA) designed to be programmed by the end user as needed.
Sergei Skorobogatov with Cambridge University’s Quo Vadis Laboratory said his team “scanned the silicon chip in an affordable time and found a previously unknown backdoor inserted by the manufacturer.”
Skorobogatov went on to say that this backdoor could be programmed to create an advanced Stuxnet Trojan horse that could disable or disrupt millions of automated systems. The chip has a “key” that Skorobogatov says his team was able to extract, a key that could be accessed for reprogramming even after the user locked the chip with their own key.
No one at Cambridge can say with absolute certainty that the backdoor originated with the Chinese manufacturer and not with the American designer. The PA3 may have been designed with the backdoor included as an integral part of the chip and was meant to be constructed with a backdoor in place.
Alec Muffett, writing for ComputerWorldUK, stated that the backdoor is a serious concern, but claims that making use of the backdoor would not be an easy task. Muffett says that associated security measures would have to be overcome, hardware would have to be accessed, and some very high-tech equipment would have to make a physical connection to actually make reprogramming possible. Such an endeavor, he says, would be on the same level as a “Mission Impossible” scenario.
The PA3 is considered to be one of the best military-grade microprocessors available today and is used in military weapons, guidance systems, flight control networks, and communications. Nuclear power facilities, power distribution grids, public transportation systems, and automotive components also make use of the PA3.
While discovery of this backdoor is a concern, any unauthorized reprogramming efforts appear to be reasonably unlikely and much less of a threat than initially believed. From a real-world perspective, the chip is in widespread use and replacing all of those now in use is a virtual impossibility. And besides, it’s also realistic to believe the chip was designed to have a backdoor in place.
Of course, the possibility that cyber warriors somewhere in the world can exploit this backdoor cannot be lightly dismissed. Finding a backdoor feature in a chip of such vital importance does call into question the reliability and security of critical electronics everyone in the world relies on to energize the modern world we live in.