Electro-optical (EO) systems are providing essential capabilities for improving security, counter terror and combating crime. Advancement in this field include smarter video surveillance systems, empowered by automated ‘video analytic’ systems managing massive flows of multiple sensors into a clear situational picture. Thermal imaging is also improved with lightweight, compact and cost effective uncooled sensors (bolometer type), used in surveillance equipment, weapons sights, night observation devices, payloads for unmanned systems etc.
On other fields, powerful image processing is harnessed for biometric identification, analyzing facial details in real-time to assist, and in certain conditions, replace human gatekeepers and attendants.
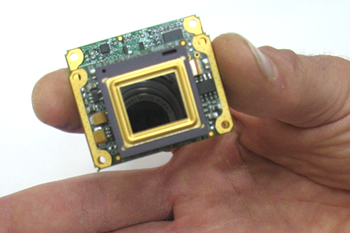
At Milipol 2009 OPGAL is introducing the ‘Compact-Eye’ (seen in the photo above), an ultra-compact thermal imaging engine designed for low-power applications. It is based on a state-of-the-art 384 x 288, uncooled 8-14μ microbolometer detector, with a 25 micron pitch. The miniature features make it suitable for portable IR applications and for thermal camera integrators seeking reduced space, weight and power requirements.
Typical uses are in surveillance systems and border security. The engine comes with an effective anti-blooming mechanism, integral x2 and x4 digital zoom and employs proprietary algorithms proven effective under poor visibility conditions. The system also employs high-resolution graphics software and flexible signal processing capabilities.
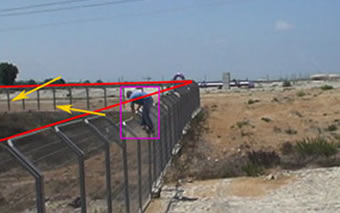
Another innovative electro-optical system is the ‘virtual wall’ from Magna BiScopic Protection (BSP). The company has developed a range of security applications based on the BSP patented principle, performing perimeter protection, surveillance and patrol as well as for use for airport safety and security. To facilitate high probability of detection at very low false alarm rate, Magna employs a combination of different methods of operation, among them the company’s patented Three Dimension Motion Detection (TDMD) and BiScopic Protection. The company is offering these systems under several product lines including the Hawk and Optical Watch Line (OWL) family, creating a ‘virtual wall’ generating an invisible trip line around the protected area, while the EAGLE family offers scanning biscopic protection for the defense of fenced-in areas and entrances. (read more…)
Security personnel are faced with an overwhelming volume of video and data, making it difficult to pinpoint events of genuine importance. Automated video analytical systems can help organize the information flow, to prioritize such vast amounts of video and data, for effective decision-making and faster and timely reaction. They enable security officers to focus on deterring and managing threats, rather than scanning banks of video monitors in trying to detect these. (read more…)
Face recognition ID (FRID) is already endorsed by major industry and government agencies as the leading biometric ID technology. When providing a high level of positive ID, Facial recognition is more user-friendly and less intrusive than other biometric identification systems such as iris or fingerprint authentication. Deployed at a point-of-service to facilitate identification of customer’s identity, such systems are offering significant advantages for security and law enforcement. A typical system offered by C-True is combining image capture and display and processing with face recognition technology. Initiating a dialog with a new customer, the system performs a quick 3D scan of the subject’s face, employing an algorithm that analyzes facial features and assigns the persons a unique ID. (read more…)
Better Vision for the Snipers
A newcomer to Milipol, the Israeli company ‘Pulse Inteco’ is introducing its compact, lightweight fire-control system, designed for sniper rifles, grenade and rocket launchers. The system incorporates a single-pulse laser rangefinder operating in an eye-safe spectral range (invisible to night vision devices) integrated with a sniper’s telescope and fire control computer. The laser accurately measures distance to the target. The ballistic computer calculates the elevation angle, moving the scope’s displayed reticule to compensate for the ballistic trajectory. At night, the system matches with a night vision viewing device for enhanced operation.
At Milipol 2009 Meprolight is announcing the NOA (picture above), the latest weapon sight added to the company’s night sights portfolio. NOA is an uncooled thermal weapon sight, incorporating a mission computer turning the sight into a powerful surveillance and intelligence collection tool. The sight supports X4/X7 magnification with image clarity and precision enabling a sniper to detect a human target at 1500 meters. Static targets can even be detected behind camouflage, battlefield obscurants, in adverse weather and total darkness.