In the spring of 2007, as the first wave of new combat brigades arrived in Baghdad to execute President George W. Bush’s troop surge, an Army lieutenant colonel named Paul Yingling former deputy commander of the 3rd Armored Cavalry Regiment, who served two tours in Iraq, wrote a highly intriguing article in the Armed Forces Journal, criticizing US military leadership in Iraq. It was an extraordinary piece of writing by a serving military officer.
The debate which followed Colonel Yingling’s article is in itself of significant interest, as it displays a growing unrest within the US Army’s officer corps in the conduct of counter- insurgency (COIN), or asymmetric warfare, in Iraq and in Afghanistan. In his article Colonel Yingling argues that the US general corps needs to be overhauled because it failed to anticipate the post-invasion insurgency in Iraq, and because of its reluctance to admit the onset of such an insurgency in 2004. He likens Iraq to Vietnam, stating that “for the second time in a generation, the United States faces the prospect of defeat at the hands of an insurgency”.
Because Vietnam was commanded by different generals than Iraq, he concludes that the US generalship, as an institution has failed, though not individual generals. He proposes that Congress takes more interest in military affairs, especially when confirming generals to their combat related posts. Generals, in his opinion, need to be aware that future US wars won’t involve one big enemy army – that is, they need to admit that realities have changed since the World Wars. He states that the US needs generals to be more creative, as well as better understand the history of war, international relations, and foreign cultures.
The colonel actually spares no small talk on his critics: “It is unreasonable to expect that an officer who spends 25 years conforming to institutional expectations will emerge as an innovator in his late forties Actually senior officers suffer from conformity, lack of vision, and lack of creativity”, the colonel claims. Moreover, “Events over the last two decades demonstrate that insurgency and terrorism are the most likely and most dangerous threats our country will face for the foreseeable future. Our enemies have studied our strengths and weaknesses and adapted their tactics to inflict the maximum harm on our society.”
A new look at Counterinsurgency?
Colonel Yingling’s unprecedented “j’accuse” caused quite a ruckus among his fellow compatriots and the media, which obviously had a field day. But it also triggered an important debate, in which some of the more important issues in modern warfighting came to light and not only within the US Army. The ongoing arguments, which reflect various views over tactics used, represent an attempt to answer a searing question: “What are the lessons of Iraq?” Ultimately, the answer will probably emerge in and endless debate, which will continue long after the troops are withdrawn from the battlefield.
Counterinsurgency is a much-disputed concept, but it refers to methods of warfare used to divide a civilian population’s political and sentimental allegiance away from a guerrilla force. From the start of the Iraq war, a cadre of warrior-thinkers in the military has questioned the use of tactics that focus more on killing enemies than giving the Iraqi population reasons not to support terrorists, insurgents and militias.
“We don’t just talk about the enemy, we talk about the environment,” explained Lt. Gen. Ray Odierno, until recently the corps commander in Iraq, in a lecture at the Heritage Foundation. Even the staunchest critics assert that early use of a sound counterinsurgency strategy could have won the Iraq war itself. But many analysts agree, based on the visible decline in violence in Iraq during the last half of 2007 that a better counterinsurgency strategy would have allowed the war to have been less costly than it proved to be.
There are critical lessons that the counterinsurgency proponents believe need to be applied – first in Iraq and Afghanistan, and then institutionalized throughout the entire military establishment. To them, institutionalization is key: it’s something that the military avoided in the generation between Vietnam and Iraq, so as not to entangle the U.S. in any more counterinsurgency campaigns – even as adversaries adjusted to America’s conventional military dominance. The fact is that during the Clinton era, the Pentagon focused on buying more high-tech jet fighters, sophisticated communications systems, and sensors, all geared towards high intensity conflict, while placing very little emphasis on the tactical needs in low-intensity warfare, which was already in the cards, in the turn of the new century. A similar trend emerged clearly in the Winograd Commission findings, which examined the Israeli defense community decisions in preparing the IDF for a low-intensity conflict with Hezbollah during summer 2006.
 Within the US Army there are already some early signs, small as they still are, of an institutionalization change. General David Petraeus, an officer with considerable experience in counterinsurgency warfare, has become a significant figure opting for profound changes in the army’s tactical and operational doctrine. Before the general left for his overall command in Iraq, Petraeus commanded the Combined Arms Center at Ft. Leavenworth, a bastion of the Army’s institutional knowledge, where he established the first counterinsurgency course for young officers. Another important development is the fact, that the Army recently raised stability operations to equal importance with offensive and defensive operations in its official Operations manual, FM 3-0 – adding a brand new category of warfare for the first time in the Army’s 232-year history. But not all is going smoothly yet, as it takes time to make new operational concepts to be fully accepted within a deeply conservative and highly institutionalized organization like any professional Army. There are already some “seniors” in the service, which regard the “newcomers” as insufficiently “mature” to radicalize long established operational traditions. In their view, the “young and eager counterinsurgents” , are still regarded in outsider status, which causes them naturally, to consider themselves a besieged minority inside the “Big Army “.
Within the US Army there are already some early signs, small as they still are, of an institutionalization change. General David Petraeus, an officer with considerable experience in counterinsurgency warfare, has become a significant figure opting for profound changes in the army’s tactical and operational doctrine. Before the general left for his overall command in Iraq, Petraeus commanded the Combined Arms Center at Ft. Leavenworth, a bastion of the Army’s institutional knowledge, where he established the first counterinsurgency course for young officers. Another important development is the fact, that the Army recently raised stability operations to equal importance with offensive and defensive operations in its official Operations manual, FM 3-0 – adding a brand new category of warfare for the first time in the Army’s 232-year history. But not all is going smoothly yet, as it takes time to make new operational concepts to be fully accepted within a deeply conservative and highly institutionalized organization like any professional Army. There are already some “seniors” in the service, which regard the “newcomers” as insufficiently “mature” to radicalize long established operational traditions. In their view, the “young and eager counterinsurgents” , are still regarded in outsider status, which causes them naturally, to consider themselves a besieged minority inside the “Big Army “.
Even elements in the Marine Corps, traditionally known as open minded, people are somewhat skeptical over the newly emerging trend, which they fear could sap some of their specific operational requirements. Present Marine Commandant, Gen. James Conway, and surprisingly even slighted counterinsurgency in his latest public statements as a “lesser-included” mission of the Marine Corps. General Conway commanded the 1st Marine Expeditionary Force during Operation Vigilant Resolve in Fallujah and rumors then spread that the Marines were criticizing army tactics in the battle, which the general vehemently denied: in his words : ” We shall follow our orders”, as he and his troops did indeed in the controversial battle of Fallujah.
But the counterinsurgency strategy still encounters opposition within the Army. Even with General Petraeus promoted to the helm of the Army’s lucrative promotions board, some of his compatriots wondered why, for example, a veteran colonel named H.R. McMaster, who successfully implemented a counterinsurgency strategy in the Iraqi city of Tal Afar in 2005 at the command of the 3rd Armored Cavalry Regiment, had been surpassed and will he ever receive his first star?
Still something seems to give after all, in the bureaucratic grapevine from the top down. While the long established procurement priorities of the Army have not dramatically changed since Operation Iraqi Freedom (OIF), nor have the ground services gotten a significantly bigger piece of the budgetary pie “The Army has gotten a much bigger share than it has traditionally because of the costs of the operations in Iraq and Afghanistan, where it plays the dominant role,” said Steve Kosiak, a defense analyst at the Center for Strategic and Budgetary Assessments. “In terms of the ‘base’ budget – i.e., the budget exclusive of war costs – its share has grown as well, but only very modestly. But it still receives slightly less than the Navy and Air Force.” Kosiak warns.
 Nevertheless, there are counter critics in the ongoing debate as well. One of them is Yingling’s brother officer, anArmy lieutenant colonel Gian Gentile, who served two tours in Iraq commanding an armored cavalry squadron. The colonel considers the counterinsurgents’ sense of besiegement to be virtually ludicrous. To him, the military is undergoing a “titanic shift” in favor of counterinsurgency with little debate over its in-depth implications. “I worry about a hyper-emphasis on COIN and irregular warfare,” he claims in another article in the Armed Forces Journal, “with less mechanization, less protection and more infantry on the ground walking and talking with the people, it’s a potential recipe for disaster if our enemies fight the way Hezbollah did against the Israelis in the summer of ‘06.” Colonel Gentile warned. Gentile said that units – including his own – applied COIN practices throughout the war, but he observed that in Iraq, conditions got worse, not better.
Nevertheless, there are counter critics in the ongoing debate as well. One of them is Yingling’s brother officer, anArmy lieutenant colonel Gian Gentile, who served two tours in Iraq commanding an armored cavalry squadron. The colonel considers the counterinsurgents’ sense of besiegement to be virtually ludicrous. To him, the military is undergoing a “titanic shift” in favor of counterinsurgency with little debate over its in-depth implications. “I worry about a hyper-emphasis on COIN and irregular warfare,” he claims in another article in the Armed Forces Journal, “with less mechanization, less protection and more infantry on the ground walking and talking with the people, it’s a potential recipe for disaster if our enemies fight the way Hezbollah did against the Israelis in the summer of ‘06.” Colonel Gentile warned. Gentile said that units – including his own – applied COIN practices throughout the war, but he observed that in Iraq, conditions got worse, not better.
That realization turned Gentile from an ardent COIN practitioner to a COIN skeptic. Counterinsurgency, he now believes, has a role in a modern military, but an excessive focus on it serves as an alibi to avoid recognizing that the U.S. military is not omnipotent. “I think Andrew Bacevich (a former army colonel and international relations professor), at the policy-strategy level, has basically nailed it,” Gentile said, referring to the retired Army colonel who contends that Iraq is an irredeemable strategic mistake. “He points out the limits of what American military power can accomplish.”
Striking that balance is the central question in U.S. military circles in 2008, and the counterinsurgency community is at the heart of it. In this argument between two respected senior officers, the next major debate over U.S. defense policy can be gleaned. Yingling speaks for an ascending cadre of young defense intellectuals, most of whom are Iraq and Afghanistan veterans, who assert that the U.S. military must embrace principles of counterinsurgency if it is to triumph in the multifaceted fight against global terrorism. While still at odds, in their respective views ,both based on their common experiences in combat, the two colonels readily agree, that the military still suffers from lack of intellectual reassessment. “We don’t agree on every point,” Yingling said, “but we do agree on the need for a rigorous debate in the Army about what kind of threats we face and what the Army needs to defeat them. I would not want the Army to rigidly adopt COIN doctrine in the same way we rigidly adopted high-intensity mechanized state-on-state warfare.”
Defense Update would like to open a discussion on this highly intriguing issue, which affects not only the US Army, but also all military forces engaged, one way or other in counterinsurgency and asymemtric warfare against terrorists.
 The first AquaShield system was installed in 2007 to protect an oil terminal in Poland. In 2008 the company supplied systems worth $8 million, including a complete harbor surveillance system capable of detecting, tracking, classification and promptly responding to above-water as well as underwater threats. “We are currently experiencing a growing demand for our products due in part to the surge in terrorist activities around the globe.” Dan Ben-Dov, DSIT’s VP Sales & Marketing told Defense-Update. The systems, to be used at undisclosed locations in Asia, will guard and protect the customer infrastructure from underwater intrusion and sabotage. The system will include multiple DDS units, which will be combined and integrated into a comprehensive surveillance system. He said the system has proved extremely reliable, operating around the clock.
The first AquaShield system was installed in 2007 to protect an oil terminal in Poland. In 2008 the company supplied systems worth $8 million, including a complete harbor surveillance system capable of detecting, tracking, classification and promptly responding to above-water as well as underwater threats. “We are currently experiencing a growing demand for our products due in part to the surge in terrorist activities around the globe.” Dan Ben-Dov, DSIT’s VP Sales & Marketing told Defense-Update. The systems, to be used at undisclosed locations in Asia, will guard and protect the customer infrastructure from underwater intrusion and sabotage. The system will include multiple DDS units, which will be combined and integrated into a comprehensive surveillance system. He said the system has proved extremely reliable, operating around the clock.




 Nevertheless, there are counter critics in the ongoing debate as well. One of them is Yingling’s brother officer, an
Nevertheless, there are counter critics in the ongoing debate as well. One of them is Yingling’s brother officer, an
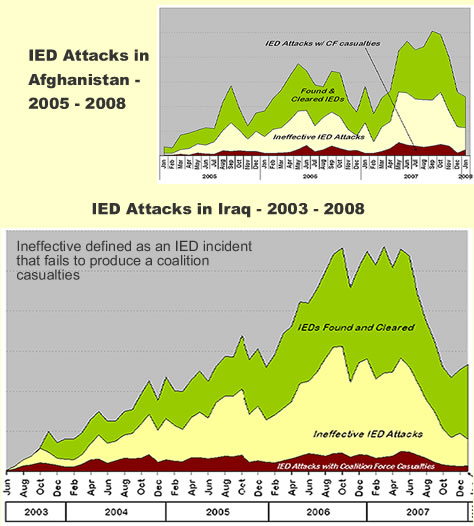






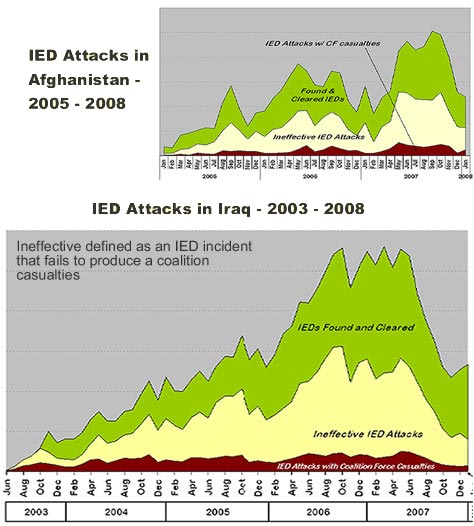
 Text based information resources such as email and articles can be used with text processing applications such as SAS Text Miner (picture here), to uncover information hidden in document collections, by analysing a elements with common intelligence values and predictive models.
Text based information resources such as email and articles can be used with text processing applications such as SAS Text Miner (picture here), to uncover information hidden in document collections, by analysing a elements with common intelligence values and predictive models.