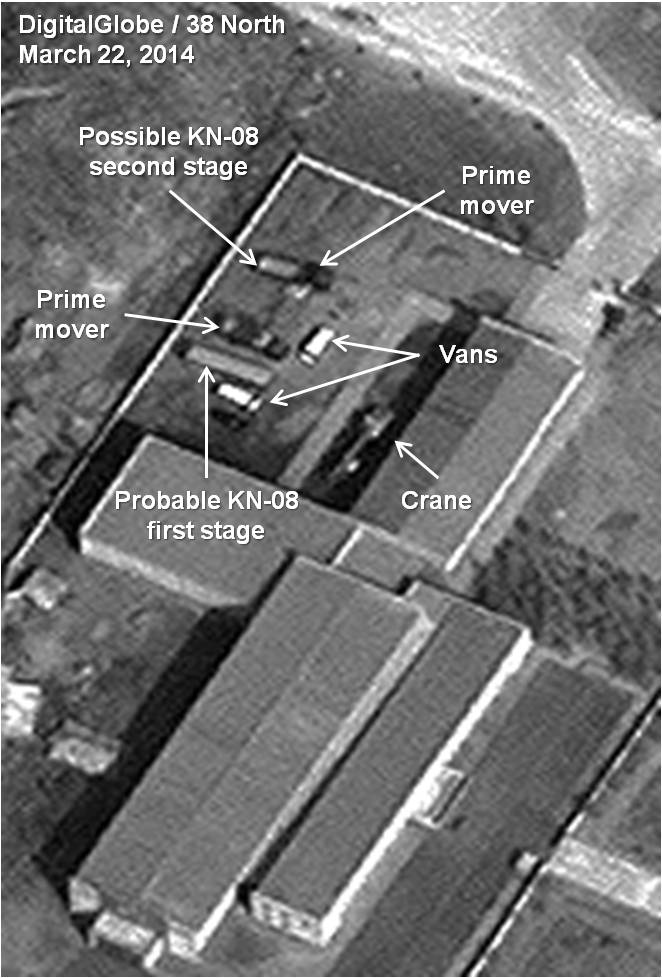
Israel
Developments in IDF cyber campaign for officials
The Israeli Defense Force (IDF) exposed its in-house newsfeed, which is published through Ynet. The site is referred as “inet” and operated under the intelligence army unit for over a year and a half. The goal is to provide online strategic security updates to the Prime Minister, Defense Minister, Chief of General Staff, and several hundred more authorized personnel. The site supplies unclassified information and live video surveillance cameras and satellites. An example for “inet” was Operation Full Disclosure, were visitors received live and developing updates during the operation, long before publication occurred to the general media.
It has been exposed that attacks had been made against the IDF cyber war room and the IDF. Apparently in the last year, a tank and an F-16 were infected by random malware. However, the cyber-attack was never confirmed by another source, news agency, or the military. Colonel Ronen Schneider, Head of the C4I Department, stated on the C4I military base that IDF computers in tanks are exposed to cyber-attacks like any other computer; therefore, the IDF is planning to open a cyber body in order to defend on the land branch weapons as well.
Revelations about secret Israeli cyber unit, S-74
A month after #OpIsrael began, revelations about the power of Israel’s cyber security revealed a secret unit in the Israeli Security Agency (Shabak), referred to as the S-74 unit. S-47 tracks movements of Anonymous worldwide and prevents cyber-attacks from disrupting the system before they occur by performing operations in networks and computers worldwide and collecting data this way. An S-74 member explained: “we follow networks around the world closely and collect intelligence through HUMINT and SIGINT.” Further, staff of S-74 run through constant simulations to prevent real time attacks, citing timing is critical. Simulations and research were an essential part of preparing for the #OpIsrael attacks. Because of the quantity of attacks, it is difficult to diagnosis how real the threat is; however, the Shabak has the capabilities to test and analyze all invading disruptions. The unit developed “tools to identify anomalous networks, abnormal movements, and to isolate and contain them,” the Shabak source explained. He adds that they provide information to CEOs for them to increase cyber security, such as the Israel Railways office with safe measurements in place already. Yet, this level of cyber intelligence has demonstrated to be essential, as the S-74 unit was accredited for providing the information necessary to kill senior Hamas operative Hamza Abu Aljeha in Jenin.
USA
Heartbleed bug takes general public by storm
Finnish computer experts discovered a crucial security hole in the encrypting software OpenSSL, referred to as the Heartbleed bug. The National Security Agency (NSA) revealed prior knowledge to the bug for two years. OpenSSL is used by two thirds of all Internet browsers and is supposed to make passwords and email contents unreadable for third parties. The Heartbleed bug deceives servers into draining data from its memory, giving hackers (aware of the vulnerability) access to sensitive information such as credit card numbers, email contents, and passwords. Heartbleed was introduced as part of an upgrade in 2011, which allowed criminals to disguise themselves as another website to acquire data. Antti Karjalainen, one of the IT experts who found the hole, explained: “They are used for proving that you are who you really say you are. So this was potentially the worst vulnerability in the history of the Internet.” Affected platforms include Google, Facebook, Yahoo, Flickr, Twitter and Tumblr. Facebook reported a spike in password changes in response to the bug, while Google and Yahoo declined to comment, though it appears major companies took the threat extremely seriously. Two-factor authentication, forcing users to have two separate pieces of confirmation, is recommended to rid of Heartbleed and other similar bugs, while password management apps have had a surge in response to the bug. NSA defended its position by not revealing the bug to the public in order to examine and explore its vulnerabilities and see if significant risk could occur through an adversary group. “Too little transparency and citizens can lose faith in their government and institutions, while exposing too much can make it impossible to collect the intelligence we need to protect the name. We weigh these considerations through a deliberate process that is biased toward responsibility, disclosing the vulnerability, and by sharing… we want everyone to understand what is at stake,” NSA spokesperson declared. It appears Heartbleed has begun a transition in the general public’s response to its own cyber security as well as the American government exploiting major flaws for intelligence purposes.
FBI informant related to campaign of cyber-attacks against foreign countries
Former Anonymous member and now informant working for the FBI, Hector Xavier Monsegur alias “Sabu,” was shown related to cyber-attack campaigns conducted in 2012 targeting foreign websites, after his arrest speculating the FBI used him to gather data on foreign countries. According to the New York Times, documents revealed Monsegur’s involvement in targeting foreign websites hosted in Brazil, Turkey, Iran, Syria, and Pakistan, as well as government websites such as the Polish Embassy in Britain. Monsegur extracted bank records, login information, etc. and upload the information to a FBI server. He received assistance from other members of Anonymous by informing them of weaknesses in the foreign websites. According to court documents, to conduct these cyber espionage attacks, Monsegur exploited hosted software vulnerabilities and extracted data in over 2,000 foreign websites, which was then forwarded to a server controlled by the FBI. Monsegur, who is one of the founders of LulzSec (an affiliate to Anonymous), was first arrested by the FBI on June 7, 2011, and rather than sent to prison and abandoning his daughter, he agreed to work as an informant for the FBI against Anonymous and LulzSec. Though the FBI has taken no credit in the attacks, it is not surprising to see cooperation between government agencies and hackers, but in reality, many governments use hackers to conduct cyber operations against other hacker organisation or foreign governments to gather intelligence. These cyber operations are commonly referred to as “an offensive cyber policy.”
Hagel urges trilateral work for threat assessment, cybersecurity
During his first meeting with Canadian Defense Minister and Mexico’s Secretary of National Defense and Naval Secretary, Defense Secretary Chuck Hagel stated: “Cybersecurity is another common challenge that knows no borders…. Each U.S. defense institution works individually to address potential cyber threats and the Defense Department has worked to elevate the importance of cybersecurity in the National Security Strategy.” He noted, “While our defense institutions do not have the lead in our respective countries for cybersecurity, we all share a common interest in [protecting] military communications.” He proposed cooperation in order to establish a cyber working group to identify potential opportunities to share best practices and lessons learned.
Russia
U.S. scared of Russian cyber-attack against financial system
It is reported that American authorities fear cyber-attacks from Russia hackers due to the implementation of new sanctions against the country. U.S. officials and security experts explained that malicious attempts of interference in the system of banks and other companies in the U.S. are to be expected in response to Western sanctions. However, the Financial Services Roundtable organization is confident these actions on the part of Russia are expected to be background of the conflict, which was aroused by recent political inconsistency between Ukraine and Russia.
Middle East
Saudi Arabia ranks second in Gulf for exposure to cyber attacks
A report by Kaspersky Lab, recently concluded among Middle Eastern countries, the United Arab Emirates came first in exposure to cyber-attacks with 38, followed by Saudi Arabia with 29% rate. Egypt came third with 10%, followed by Qatar with 9.5%, and Kuwait, at just over 6%. Less than 1% of financial attacks in 2013 targeted the region, which were mostly launched in a bid to obtain usernames, passwords, and credit card details. Attackers targeted e-mails potentially sent by official government bodies, such as banks, in order to receive details, the report explained.
Iran calls for broader int’l cooperation in campaign against cyber crimes
Head of Iran’s Cyber Police (FATA) General Seyed Kamal Hadianfar recently said in meeting with the representative of the UN Office on Drugs and Crime (NODC) to Tehran, Leik Boonwaat, there is a collective need globally to prevent the spread of cyber-crimes. During the meeting, General Hadianfar stated: “Effective international cooperation is an important and determining factor in prosecuting and confronting cyber-crimes.” For his part, Boonwaat vowed the UNODC would seriously pursue a campaign against cyber-crimes in Iran. Eight regional countries, representatives of Interpol and the NODC, and Iran’s Cyber Police chief took part in the conference.
SEA attacks RSA conference
The RSA conference website was the next target for the Syrian Electronic Army (SEA). SEA chose the RSA conference because of an uploaded video depicting methods to prevent cyber-attacks from SEA, presented by Ira Winkler. In the video, Winkler discussed rumors of previous members from SEA and stated the cyber-attacks are “low tech” attempts, calling SEA cockroaches of the Internet. SEA defaced the website with the following message: “Dear Ira winkler, Do you think you are funny? Do you think you are secure? You are NOT….” Winkler, in response to the defacement, blogged that the SEA was unable to literally breach the RSA conference website or the hosting service, but conducted a phishing attack against the DNS service company the hosting service uses. Nevertheless, SEA has not been deterred and continues to threaten Winkler and the RSA conference.
China and APAC
China spying operation against Australian Parliament
According to an Australian newspaper, in 2011 a cyber-attack occurred on the Australian parliamentary computer network, causing weaknesses allowing the Chinese intelligence services to gain access to Australian parliamentary information. The computer network of the Australian Parliament is a private network containing emails and unclassified documents used by federal lawmakers. It can however sometimes contain sensitive discussions between MPs. By having access to the network, China gathered significant information about the political and social links of and to the Australian leaders. Indeed, different intelligence agencies believe China intends to use this information to establish a map with Australian relations. Australia is one of the top countries for communication intelligence and cyber security. However, it seems they continue to have a weakness in national cyber security. For China, this cyber spying operation is just another major cyber spying campaign conducted by the Chinese government and state sponsored hacking groups.
Europe
UK: A new chief to lead British communication intelligence agency
Robert Hannigan, a senior British civil servant was chosen to be the next chief of the Government Communications Headquarters (GCHQ), which is the British intelligence agency responsible for SIGNIT, Internet surveillance, and cryptanalysis. His appointment was announced last week, and he will begin in August, 2014. He joined the civil service after working in the private sector and held several government positions, such as Director of Communications for the Northern Ireland Office; Head of Security, Intelligence, and Resilience at the British Cabinet Office; and finally moved to the Foreign and Commonwealth Office. By choosing Hannigan, the British government is enlisting change. The future head of the GCHQ declared that it was a “privilege” to be asked to lead GCHQ. Like the MI5 and MI6, GCHQ’s mission is to ensure the security of the United Kingdom. Its challenges include counter terrorism, drug traffic, cybercrime, and countering cyber spying activities. The GCHQ today is the second biggest communication intelligence agency after the American NSA with whom they work in close collaboration.
UK costs of preventing cyber-attacks increase
The cost of preventing cyber-attacks has risen, even though the UK has decreased the scale of attacks in the recent year. A major scale on a small organization can range from £65,000 to £115,000 and for a large organization between £600,000 and £1.15 million. Although large scale attacks have been reduced, the cost of maintaining the security has risen significantly. The survey conducted depicted a rise in attacks for smaller organizations as opposed to larger ones.
(ISC)2 launches new European qualification
A major problem for information security today is the inability countries face in fighting cybercrime as a worldwide unit. Because the crime scenes are so broad, (ISC)2 is aware of collaboration in all aspects of security, including technology, analytics, law enforcement, and business. The CCFP certificate has so far been available in the US and South Korea; however, it took more time for it to adapt in the EU, due to the law-related disparities among countries. The addition of a new certificate is a sign that cyber forensics is maturing into a serious discipline, separated from fields like data management and systems security. The applicants must hold a BA degree or regional equivalent and have at least three years of cumulative paid, full-time, professional experience in digital forensics or IT security and will be tested in six (ISC)2 common body of knowledge (CBK) domains: legal and ethical principles, investigations, forensic science, digital forensics, application forensics, and hybrid and emerging technologies. The first exam took place on April 30 at Pearson VUE test centers in the UK.
DARKNET
New cyber search engine for buying illegal products
The black market upgraded to a new search engine called “Grams.” The new dark website: (http://grams7enufi7jmdl.onion), allows users to buy illegal drugs, guns, fake IDs, or other contraband items online. The attraction of “Grams,” as opposed to other search engines on the darknet, is its similarity to Google. “Grams” enables users to type in requested data through a search bar, were results appear in a matter of minutes directing the user to a series of possible links. The new site joins a long list of many search engines: Agora, BlackBank, C9, Evolution, Mr. Nice Guy, Pandora, The Pirate Market, and SilkRoad2. The“Grams” creator, who refers to himself as Gramsadmin, wrote on Reddit: “I am working on the algorithm so it is a lot like google’s it will have a scoring system based how long the listing has been up, how many transactions, how many good reviews. That way you will see the best listing first. I am going to add a filter market this week so a use can search only the markets they have accounts for.” It can be concluded that “Grams” is meant to provide user convenience and improve web surfing experience in the growing darknet.
 About the Cyber Intelligence Report:
About the Cyber Intelligence Report:
This document was prepared by The Institute for National Security Studies (INSS) – Israel and The Cyber Security Forum Initiative (CSFI) – USA to create better cyber situational awareness (Cyber SA) of the nature and scope of threats and hazards to national security worldwide in the domains of cyberspace and open source intelligence. It is provided to Federal, State, Local, Tribal, Territorial and private sector officials to aid in the identification and development of appropriate actions, priorities, and follow-on measures. This product may contain U.S. person information that has been deemed necessary for the intended recipient to understand, assess, or act on the information provided. It should be handled in accordance with the recipient’s intelligence oversight and/or information handling procedures. Some content may be copyrighted. These materials, including copyrighted materials, are intended for “fair use” as permitted under Title 17, Section 107 of the United States Code (“The Copyright Law”). Use of copyrighted material for unauthorized purposes requires permission from the copyright owner. Any feedback regarding this report or requests for changes to the distribution list should be directed to the Open Source Enterprise via unclassified e-mail at: [email protected]. CSFI and the INSS would like to thank the Cyber Intelligence Analysts who worked on collecting and summarizing this report.